Introduction
This might be useful for someone. These are drafts from one of my projects for an IT company (startup) with remote employees.
In today’s digital world, IT infrastructure security is a critically important aspect for any business. Small and medium-sized companies often become targets of cyber threats due to limited resources for data protection. Here is a basic minimum set of software required to address most vulnerabilities — just a starting point.

1. Authentication and Access Management
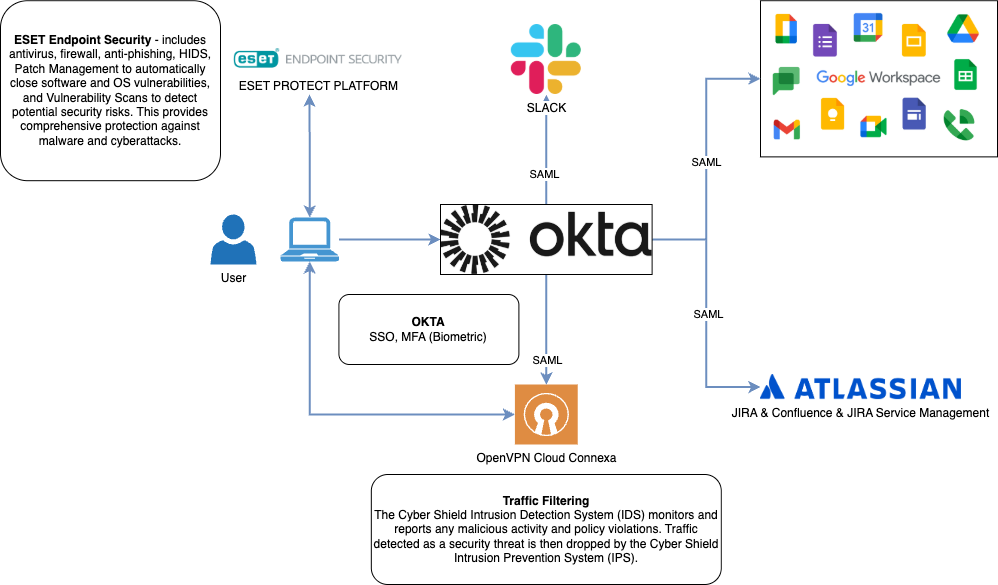
Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
One of the key aspects of security is a reliable authentication system. Using OKTA or similar solutions for access management allows you to:
- Implement a Single Sign-On (SSO) system, simplifying employee access to corporate resources.
- Apply Multi-Factor Authentication (MFA), including biometrics and OTP codes, significantly reducing the risk of credential compromise.
2. Antivirus Protection and Threat Monitoring
Comprehensive Endpoint Protection
IT companies should use antivirus software with advanced protection features. ESET Endpoint Security offers:
- Antivirus, firewall, phishing protection, and vulnerability analysis.
- Automatic patch updates for software and operating systems, reducing the risk of vulnerability exploitation.
- Suspicious activity monitoring and proactive threat blocking.
3. Encryption and VPN
Secure Access via VPN
For remote employee access, it is recommended to use a VPN with advanced encryption capabilities. OpenVPN Cloud Connexa provides:
- Secure connection to corporate resources.
- Safe browsing on the Internet.
- Support for SAML authentication, ensuring access control through OKTA.
- Minimization of traffic interception risks.
4. Network Traffic Control and Threat Filtering
Intrusion Detection & Prevention System (IDS/IPS) Integration
To prevent attacks, the implementation of Intrusion Detection and Prevention Systems (IDS/IPS) is necessary:
- IDS – analyzes network traffic and detects suspicious activity.
- IPS – blocks malicious traffic and prevents intrusion attempts.
- Deploying these solutions reduces the likelihood of successful attacks on infrastructure.
5. Corporate Services Management
Cloud Platform Integration
To ensure manageability and control, it is recommended to integrate Google Workspace and Atlassian (JIRA, Confluence, Service Management) via SAML authentication. This allows you to:
- Centrally manage access to corporate resources.
- Simplify control over employee accounts.
- Provide a fast response to security incidents.
6. Communications and Notifications
Integration with Slack
For prompt employee notifications about security incidents, it is necessary to use centralized alert systems. Slack, integrated with OKTA, can serve as an effective tool for:
- Notifications of unauthorized login attempts.
- Automatic alerts about security updates.
- Interaction with support staff.
Conclusion
IT infrastructure security is not only a mandatory protective measure but also a way to increase the trust of clients, partners, and employees. Small and medium-sized businesses can significantly enhance their security by implementing SSO (Single Sign-On), antivirus protection, VPN, traffic filtering, and centralized service management. Integrating these solutions does not require significant costs but substantially improves the company’s cybersecurity level.
This list does not include workstation encryption, awareness training, MDM, and other aspects. I will try to cover these separately.